In our increasingly interconnected world, the foundational hardware that underpins all digital activity, the humble silicon chip, is facing an unprecedented range of cyber threats. From sophisticated state-sponsored attacks to opportunistic hacks, the vulnerabilities in hardware can have catastrophic consequences, impacting everything from national security to personal privacy. This reality has ushered in a new era of paramount importance: security-aware chip design. No longer can security be an afterthought; it must be ingrained into every stage of the design process, from conception to fabrication.
The traditional approach to security often focused on software layers, firewalls, and encryption protocols. While these are undoubtedly critical, they operate on top of hardware that might itself be compromised. If the root of trust, the silicon itself, is insecure, then all subsequent layers of protection can be undermined. This is why chip design companies are now prioritizing a “shift left” in security, embedding robust protections directly into the hardware architecture.
The Evolving Threat Landscape for Hardware
The threats to hardware are diverse and constantly evolving. These include:
- Side-Channel Attacks: These attacks exploit unintended information leakage from a physical implementation of a cryptosystem. This could be power consumption, electromagnetic emanations, or even timing differences, potentially revealing secret keys or sensitive data.
- Fault Injection Attacks: By deliberately introducing faults (e.g., voltage glitches, clock glitches, laser attacks) into a chip during operation, attackers can manipulate its behavior, bypass security checks, or extract cryptographic keys.
- Reverse Engineering and Tampering: Malicious actors can analyze the physical structure of a chip to understand its functionality, discover vulnerabilities, or even inject malicious hardware Trojans during the manufacturing process.
- Supply Chain Attacks: With globalized manufacturing, a chip can pass through many hands before reaching its end-user. This provides numerous opportunities for malicious insertion or alteration at various stages, making supply chain security a critical concern for chip design services.
- Intellectual Property (IP) Theft: The design of a chip is immensely valuable, and protecting this IP from theft or unauthorized copying is crucial for businesses.
Principles of Security-Aware Chip Design
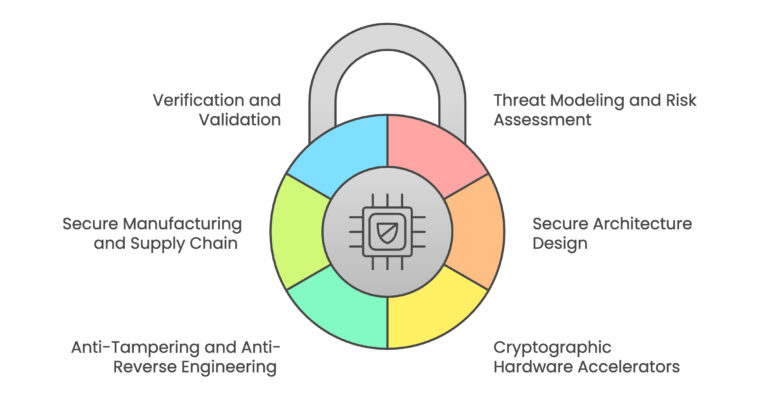
Addressing these threats requires a multi-faceted approach, integrating security considerations throughout the entire chip design lifecycle.
1. Threat Modeling and Risk Assessment
Before a single line of code is written or a transistor laid out, a comprehensive threat model must be developed. This involves identifying potential attackers, their motivations, capabilities, and the assets they might target. A thorough risk assessment helps prioritize security measures, focusing resources on the most critical vulnerabilities.
2. Secure Architecture Design
Security features should be fundamental to the chip’s architecture, not bolted on later. This includes:
- Hardware Root of Trust (HRoT): A trusted hardware component that serves as the foundation for all security operations. It verifies the integrity of firmware and software, ensuring that only legitimate code runs on the device.
- Isolation and Segmentation: Designing the chip to isolate sensitive components (e.g., cryptographic engines, secure memory) from less secure ones prevents an attack on one part from compromising the entire system.
- Memory Protection Units (MPUs) and TrustZone-like Architectures: These features create secure execution environments, separating trusted code and data from untrusted applications.
- Physical Unclonable Functions (PUFs): PUFs leverage inherent, uncontrollable manufacturing variations in silicon to generate unique, device-specific cryptographic keys. This provides a robust, hardware-derived identity that is extremely difficult to clone.
3. Cryptographic Hardware Accelerators
Implementing cryptographic algorithms in dedicated hardware accelerators offers significant advantages over software-based solutions. Hardware implementations are typically faster, more energy-efficient, and inherently more resistant to side-channel attacks. These accelerators are essential for secure communication, data encryption, and authentication.
4. Design for Anti-Tampering and Anti-Reverse Engineering
Preventing physical attacks is paramount. Techniques include:
- Obfuscation: Making the chip’s internal structure harder to understand for reverse engineers.
- Sensors and Active Shielding: Integrating sensors that detect tampering attempts (e.g., voltage changes, light exposure, decapsulation) and trigger defensive mechanisms, such as immediate data erasure.
- Secure Packaging: Using tamper-evident or tamper-resistant packaging to deter physical access to the chip.
5. Secure Manufacturing and Supply Chain
The manufacturing process itself presents vulnerabilities. Secure practices include:
- Trusted Foundries: Partnering with highly secure and audited manufacturing facilities.
- Supply Chain Transparency: Implementing robust tracking and verification systems to ensure the integrity of components throughout the supply chain.
- Hardware Attestation: Verifying the authenticity and integrity of hardware at various stages, from manufacturing to deployment.
6. Verification and Validation
Rigorous verification and validation are critical to identifying and rectifying security flaws before the chip is deployed. This involves:
- Formal Verification: Using mathematical methods to prove the correctness and security properties of the design.
- Security Audits and Penetration Testing: Specialized teams attempt to find vulnerabilities in the hardware, mimicking real-world attack scenarios.
- Fuzz Testing: Injecting large amounts of random or malformed data to uncover unexpected behavior or vulnerabilities.
How Do You Protect Advanced Chip Designs from Security Breaches?
The Future of Secure Hardware
As artificial intelligence (AI) and the Internet of Things (IoT) continue to expand, the attack surface for hardware will only grow. The stakes are higher than ever, requiring continuous innovation in security-aware chip design. This includes exploring new materials, advanced cryptographic techniques, and AI-driven security analysis tools. Collaboration between academia, industry, and government will be crucial in developing standards and best practices for secure hardware.
The shift towards security-aware chip design services is not merely a trend; it’s a fundamental paradigm shift. By embedding security at the silicon level, we can build a more resilient and trustworthy digital future, protecting our data, our infrastructure, and our way of life from the persistent and evolving threat of cyberattacks.
Innovating Secure Silicon with Tessolve
At Tessolve, we understand that in today’s digital landscape, the security of your hardware is paramount. As a leading provider of comprehensive engineering chip design services, we are at the forefront of integrating robust security measures into every stage of the silicon development lifecycle. Our expertise spans pre-silicon validation, post-silicon validation, and production test, ensuring that security is not an afterthought but an intrinsic part of your product. We partner with you to implement hardware root of trust solutions, secure boot mechanisms, cryptographic accelerators, and anti-tamper features, leveraging our deep understanding of the latest security protocols and best practices. Trust Tessolve to fortify your next-generation chips against an ever-evolving threat landscape, delivering not just performance, but unparalleled security and reliability.